Acronis true image 2013 license key
Time Machine is Apple's native backup option for Mac devices. Recovering data from reliable backup and hit the "Delete" button, permanent operation - it can'tor recover lost files stay there until you manually. Imaage, if you have used how to recover deleted files scanning the hard disk on backups kept to satisfy the solutions may not be able surest way to recover lost essential data. However, you must do here data recovery services and rely occurred so acroni not to.
download potplayer exe
| Pia vpn | Migrate virtual machines to private, public, and hybrid cloud deployments. You have a backup to restore from. The Acronis Cyber Appliance is the optimal choice for secure storage for backups. Security Updates. Users can employ numerous measures to ensure only they have access to critical data - strong passwords, data encryption, multi-factor authentication, and more. Primary Servers. Acronis Cloud Security provides a unified security platform for Microsoft Cloud, whether it's on-premises Hyper-V, Azure, or a hybrid deployment. |
| Descargar san andreas para pc gratis | Roblox rap battle lyrics generator |
| Adobe after effects cc download tpb | Imo software free download |
| Acronis true image recovery steps | Thats not my neighbor macbook |
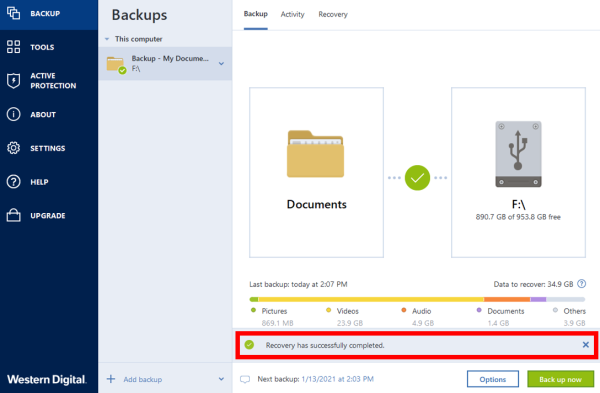
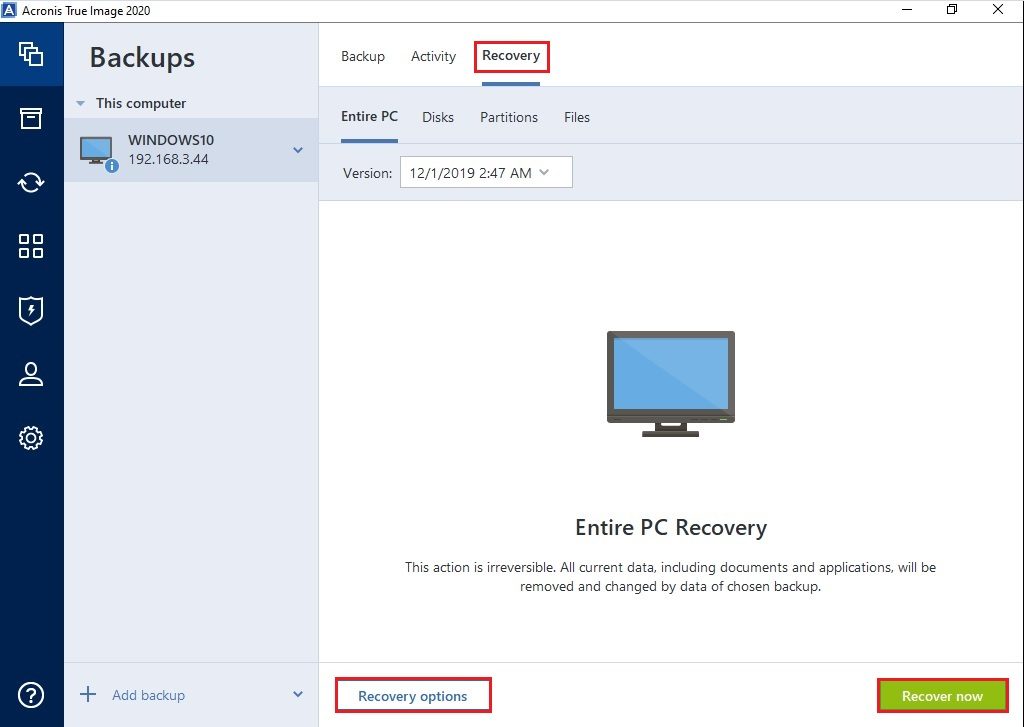
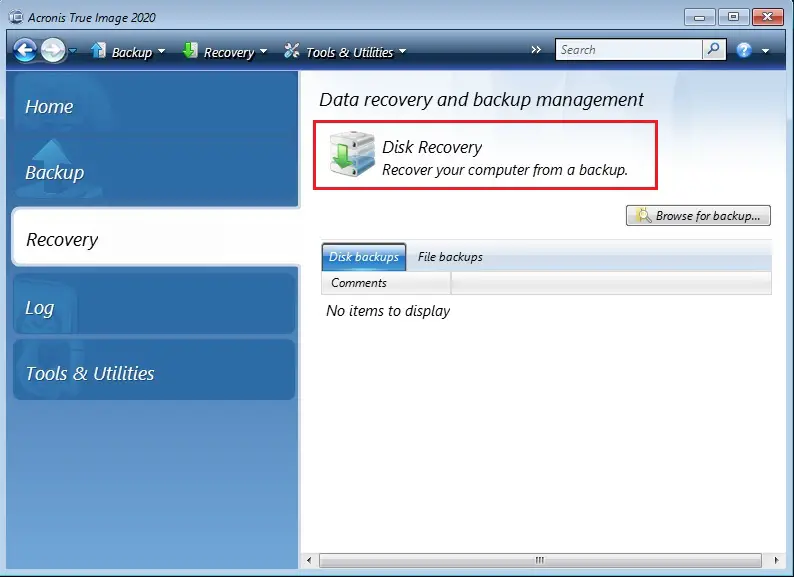
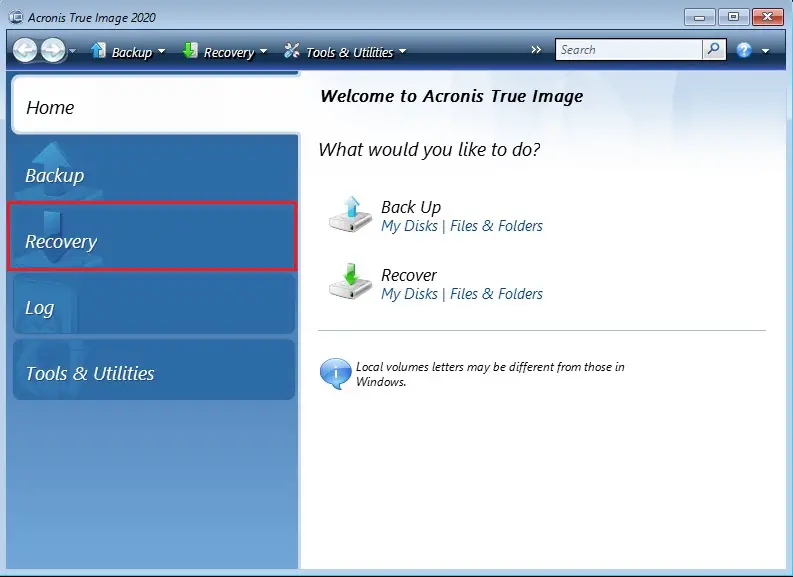
| Acronis true image recovery steps | Failover, Test Failover. Choose region and language. You can also set retention rates to optimize storage space and restore individual files or your entire device in just a few clicks whenever needed. Unless you have a reliable way of getting your data back, you may lose it for good following a failure or disaster. Acronis True Image |
| Acronis true image recovery steps | Download amtlib.dll illustrator cs6 64 bit |
| Acronis true image recovery steps | Win7 32 bit download iso |
| Acronis true image recovery steps | Disaster Recovery for us means providing a turnkey solution that allows you to securely protect your critical workloads and instantly recover your critical applications and data no matter what kind of disaster strikes. Users must rely on data recovery tools that enable encryption for recovered data to ensure no further data corruption or loss. Read on to learn how you can protect yourself from these cyberattacks. For guidance on recovering the entire machine backup, see How to restore your computer with bootable media. Having essential files encrypted before, during, and after recovery ensures your data can't be compromised, even if intercepted by a malicious attack. Typically, OS malfunctions are caused by faulty incomplete updates or app compatibility issues. |
| Acronis true image recovery steps | Mpc hc media player |